Open supply intelligence (OSINT) software program is changing into an more and more necessary device for gathering public data. This sort of software program permits customers to assemble simply accessible knowledge on people and organizations from a variety of sources — resembling serps, social media profiles, and authorities data — with the goal of making a complete image.
Superior OSINT software program can then cross-reference this knowledge to offer an correct supply of data and construct connections between totally different items of knowledge which will in any other case have gone unnoticed. In at present’s data-driven world, OSINT software program offers an indispensable useful resource for anybody seeking to acquire perception into themselves or these round them. It has additionally change into more and more standard for cybersecurity professionals utilizing it for moral hacking, penetration testing and exterior risk identification.
OSINT is a key part of Open-Supply Enterprise Intelligence (OSBI), a meta development that’s quickly rising. OSINT eliminates the hefty related value which might be prohibitive for smaller companies, and it has emerged as a gorgeous mannequin of BI as a consequence of its decrease value and scalability. At the moment, round 26% of firms use open-source instruments as a part of their enterprise technique and this quantity is prone to develop considerably sooner or later.
The OSINT market is anticipated to expertise vital progress over the subsequent 5 years–offering ample alternative for startups seeking to break into this area.
Listed here are some among the greatest open supply intelligence instruments in the marketplace:
Maltego is a flexible open supply intelligence platform that may simplify and expedite investigations. It offers entry to 58 knowledge sources and guide add capabilities, in addition to databases of as much as 1 million entities that can assist you conduct higher evaluation. Its highly effective visualization instruments additionally allow you to select from totally different layouts like blocks, hierarchical, or round graphs with weights and notes for additional refinement.
With Maltego, belief and security groups, legislation enforcement personnel and cybersecurity professionals get one-click investigation outcomes with easy-to-follow insights.
OSINT might be invaluable in a wide range of sectors, from legislation enforcement to monetary companies. Because of this the corporate additionally invests closely in offering incredible sources on OSINT instruments and strategies. Not solely are these different and complete, they’re additionally hand-picked by an knowledgeable workforce to make sure clients get the perfect out of their product. The corporate additionally gives a Maltego Basis course out there for buy on-line.
Spiderfoot is an open-source OSINT reconnaissance device with a wide range of options, together with the flexibility to acquire and analyze IP addresses, CIDR ranges, domains and subdomains, ASNs, e-mail addresses, cellphone numbers, names and usernames, BTC addresses, and extra.
Providing each a command-line interface in addition to an embedded web-server outfitted with a user-friendly GUI interface which is accessible on GitHub, Spiderfoot boasts over 200 modules which can be utilized to hold out probably the most complete actions and uncover key particulars about any goal.
It can be used to evaluate whether or not or not organizations have knowledge uncovered that would probably trigger safety breaches. All in all, it’s a highly effective cyber intelligence device able to offering invaluable insights into probably dangerous on-line entities.
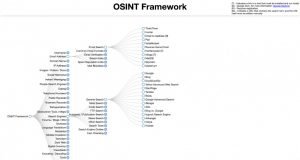
OSINT Framework is a superb useful resource for open-source intelligence gathering. It has all the pieces from knowledge sources to useful hyperlinks to efficient instruments, making it a lot simpler than making an attempt to individually analysis each program and gear on the market.
This listing additionally offers choices for working programs past Linux, offering options throughout the board. The one problem could also be growing an efficient search technique that narrows down outcomes resembling automobile registration or e-mail addresses, however with such organized sources, this finally ends up being extra of an asset than ever.
The OSINT Framework is rapidly changing into one of the vital standard options for knowledge assortment, data discovery and sorting issues out.
In at present’s digital economic system, verifying somebody’s id utilizing numerous social media and on-line platform accounts as knowledge factors is changing into extra commonplace. SEON is on the forefront of this digital id verification motion.
By tapping into its e-mail and cellphone quantity programs, your online business can entry over 50 totally different social indicators that produce a complete danger rating. These indicators not solely verify the validity of a buyer’s e-mail deal with or cellphone quantity but additionally accumulate deeper insights relating to their digital footprint.
Moreover, SEON offers companies with the pliability to implement queries manually, by way of API, and even by way of a Google Chrome extension; making it simpler to make use of and accessible.
Lampyre is a paid software designed particularly for OSINT, offering an environment friendly answer for due diligence, cyber risk intelligence, crime evaluation, and monetary analytics. It’s an intuitive, one-click software that may be put in in your PC or run on-line with ease.
Beginning with a single knowledge level resembling an organization registration quantity, full identify, or cellphone quantity, Lampyre routinely processes 100+ repeatedly up to date knowledge sources to disclose helpful data.
If wanted, you’ll be able to entry the information by way of PC software program or by way of API calls. For companies on the lookout for a complete platform to observe dangers and examine threats of varied varieties, Lampyre’s SaaS product providing – referred to as Lighthouse – permits customers to pay per API name.
Shodan is a sophisticated search engine that enables customers to rapidly determine and entry data on the know-how utilized by any enterprise. By typing in an organization identify, one can obtain detailed insights into their IoT units – resembling location, configuration particulars and vulnerabilities – grouped in accordance with community or IP deal with.
Moreover, employers could use Shodan for additional evaluation of working programs getting used; open ports; internet server sort and design language employed with excessive accuracy achieved by way of its cutting-edge software program toolsets.
Recon-ng is a strong device used to seek out data associated to web site domains. It initially began as a script, however now it has advanced right into a full framework.
When utilizing Recon-ng, customers are capable of determine internet vulnerabilities together with GeoIP lookup, DNS lookup, and port scanning. This can be very helpful for finding delicate information resembling robots.txt, discovering hidden subdomains, on the lookout for SQL errors, and retrieving firm CMS or WHOIS data.
Regardless of being extra technical in nature in comparison with different instruments out there in the marketplace, there are lots of useful sources out there that you should utilize to discover ways to take full benefit of this prime software program.

Aircrack-ng is a strong and complete safety penetration testing device utilized by digital safety professionals to check the protection of wi-fi networks. The device allows customers to gather data associated to packet monitoring, together with capturing of frames and gathering WEP IVs together with the place of entry factors if a GPS is added.
It will probably additionally conduct penetration assessments on networks and analyze the efficiency by token injection assaults, faux entry factors and replay assaults. Lastly, it will probably carry out password cracking for each WEP and WPA PSK (WPA 1 and a couple of). Aircrack-ng represents an indispensable device for assessing the potential vulnerabilities in a wi-fi community earlier than they are often probably exploited.
The flexibility of this device is a significant spotlight; it was developed primarily for Linux however might be tailored to different programs resembling Home windows, OS X and FreeBSD. Moreover, its functionality as a command line interface (CLI) offers it an edge in customization. Because of this extra superior customers can simply create customized scripts to be able to additional modify the device and tailor it to their distinctive necessities.

BuiltWith is an extremely highly effective web site detective, permitting customers to seek out out the tech stack, frameworks, plugins, and different data powering standard web sites. This may be helpful for these excited by utilizing comparable applied sciences for their very own websites.
Moreover, BuiltWith additionally lists JavaScript/CSS libraries {that a} web site could also be utilizing, offering additional granularity and perception into the structure of sure web sites. Consequently, BuiltWith shouldn’t be solely helpful for informal analysis however can be used to conduct reconnaissance on behalf of companies or organizations who must know exactly how totally different webpages are put collectively.
For added safety assurance, you’ll be able to mix BuiltWith with web site safety scanners like WPScan focusing on figuring out widespread vulnerabilities impacting a web site.

Metagoofil is a freely out there device on GitHub which focuses on extracting metadata from a wide range of public paperwork, together with .pdf, .doc, .ppt and .xls. As an extremely highly effective search engine, it is ready to unearth helpful knowledge resembling usernames and actual names related to particular public paperwork, together with server data and the trail to those paperwork.
Whereas this data presents vital dangers to organizations, the identical knowledge can be leveraged as a protection mechanism. Organizations can take proactive steps to make sure that the knowledge itself is hidden or obscured earlier than malicious actors have a chance to make use of it for sick means.

