The evolution of pc imaginative and prescient know-how has paved the way in which for modern synthetic intelligence (AI) options within the authorized business. Past conventional functions like folks detection, object monitoring, and conduct evaluation, pc imaginative and prescient has the potential to supply many extra artistic and nuanced options. On this article, we are going to discover 9 functions of pc imaginative and prescient in regulation and authorized techniques.
- #1: Legal Exercise Detection
- #2: Authorized Overview
- #3: Courtroom Proceedings
- #4: Mental Property (IP) Safety and Deepfakes
- #5: Forensic Evaluation
- #6: Face Recognition in Authorized Investigations
- #7: Digital Courtrooms
- #8: Compliance Monitoring
- #9: Proof Authentication
Deep studying object detection has been developed by researchers and adopted by pc imaginative and prescient firms to construct business merchandise that regulation establishments can make the most of. Among the most vital object detectors are YOLO, SSD, RetinaNet, and so forth. They’re based mostly on two-stage object detectors, the place approximate object areas are proposed utilizing deep options earlier than these options are used for the picture classification and bounding field regression for the thing candidate.
About us: Viso Suite is the end-to-end pc imaginative and prescient resolution for enterprises. Utilizing drag-and-drop parts, enterprises can simply create customized, no-code options to resolve enterprise challenges. To study extra, e-book a demo with the Viso crew.
Significance of Laptop Imaginative and prescient in Legislation
Laptop imaginative and prescient affords regulators a toolset for automating processes and navigating complicated authorized frameworks extra successfully. By integrating these techniques into the apply of regulation, regulators streamline enforcement processes and guarantee alignment with ever-evolving authorized requirements.
1. Legal Exercise Detection
In legal circumstances, CV algorithms ought to first acknowledge the atmosphere and the setting. Laptop imaginative and prescient surveils and analyzes pictures from totally different sources (edge units, road cameras, enterprise cameras, and so forth.). Then they proceed to know the composition of the encircling objects and distinguish between pedestrians and automobiles. The worldwide look of the scene will assist the algorithm seize particulars, together with the colour and form of automobiles, license plates, signboards, storefronts, and so forth. Something that can’t be detected within the pictures, is searched within the backend to assist regulation establishments determine, monitor, and finally – uncover the lawbreakers.

2. Authorized Overview
The standard authorized overview overview course of is understood for being marred by large volumes of paperwork. By introducing pc imaginative and prescient into the overview course of, authorized groups can reduce down on potential dangers reminiscent of language subjectivity, price and time constraints, compliance, and privateness and safety issues
Legislation companies and establishments manage and prioritize paperwork based mostly on their relevance or particular standards. CV algorithms can precisely categorize paperwork by analyzing doc traits together with buildings, structure, and formatting. When paired with predictive analytics, pc imaginative and prescient techniques can determine related patterns, relationships, and developments throughout the knowledge. This automated extraction helps save authorized practices and doc overview groups a whole bunch of hours of authorized work usually spent scanning every doc to determine these particulars.

How is that this performed? N. Huber-Fliflet, et al. utilized deep studying R-CNN for doc classification and clustering. For coaching knowledge, they utilized 235 Google pictures of paperwork with handwriting, together with handwriting notes, signatures, and hand-filled types. They utilized AI instruments to label the handwriting areas, as rectangular packing containers surrounding the area with class names. The labels have been saved in an XML file in Pascal VOC format for every of the photographs. Then they transformed the XML recordsdata right into a single CSV file after which break up it into coaching and testing units.
Lastly, the coaching and testing knowledge have been transformed into TFRecords to feed into the educational algorithm.
3. Courtroom Proceedings
Courtroom proceedings generate massive quantities of scanned paperwork that must be precisely digitized. AI-powered OCR techniques can mechanically convert scanned recordsdata into textual content, creating correct and usable transcripts of court docket proceedings. This can streamline the documentation course of and also will improve the distribution and sharing of digital content material. The digital content material is simpler to deal with, signal, and archive.
4. Mental Property (IP) Safety and Deepfakes
With the ubiquity of smartphones and social media, know-how threatens the digital content material that may now be vastly plagiarized. Many people attempt to steal the authors’ innovations, which might embrace textual content, video, audio, or pictures.
Moreover, with the rise of generative AI know-how (Chat-GPT, DALL-E), deepfakes have grow to be a technological burden that may create illicit content material with the identical which means, however a special look from the unique.
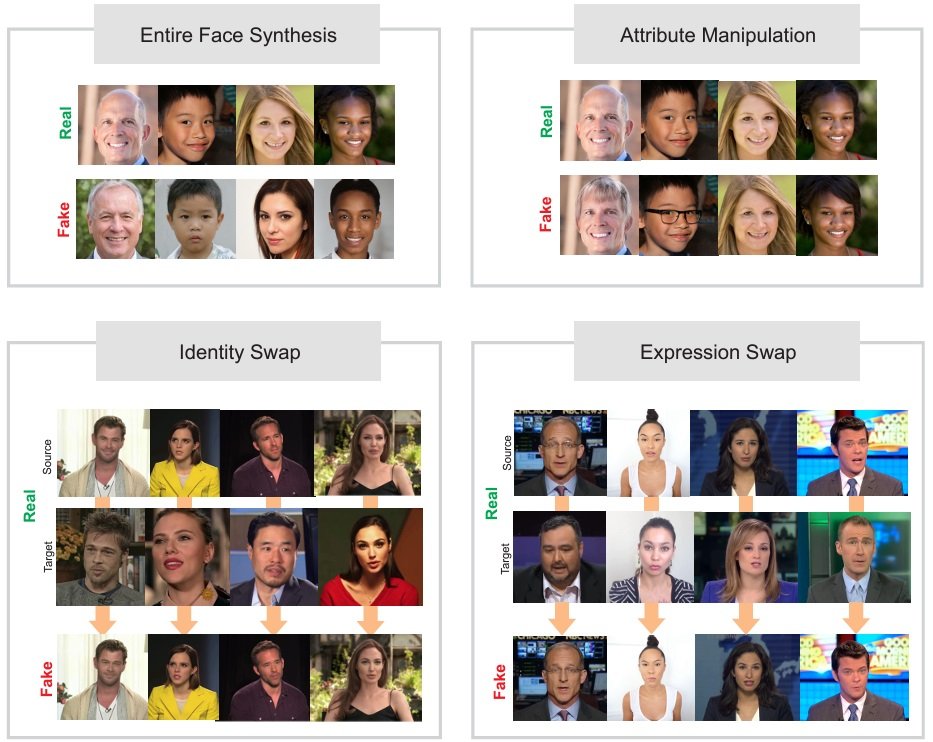
To beat this IP concern – researchers have utilized a Convolutional Neural Community (CNN) to detect plagiarized textual content and pictures in addition to problematic deepfakes on the web. X. Liu, et. al., (2020) utilized a picture copy detection scheme based mostly on the deep studying Inception CNN mannequin. Their picture dataset was transferred by a number of picture processing manipulations. The picture’s function values have been mechanically extracted for studying and detecting unauthorized digital pictures. By making use of rotation, scaling, and different content material manipulations they obtained satisfying leads to the method of detecting duplicated pictures. Additional probing with the CNN mannequin with a number of mixtures of authentic and manipulated pictures will enhance the accuracy of picture copy detection.
5. Forensic Evaluation
Crime investigation depends upon the gathering and evaluation of various kinds of proof. Impression proof, reminiscent of footprints, tire tracks, and facet marks are necessary sources of bodily proof for regulation enforcement businesses. They can be utilized to verify or reject data supplied by witnesses or suspects. In accordance with a study carried out in Switzerland, shoe prints will be present in round 35% of all crime scenes.
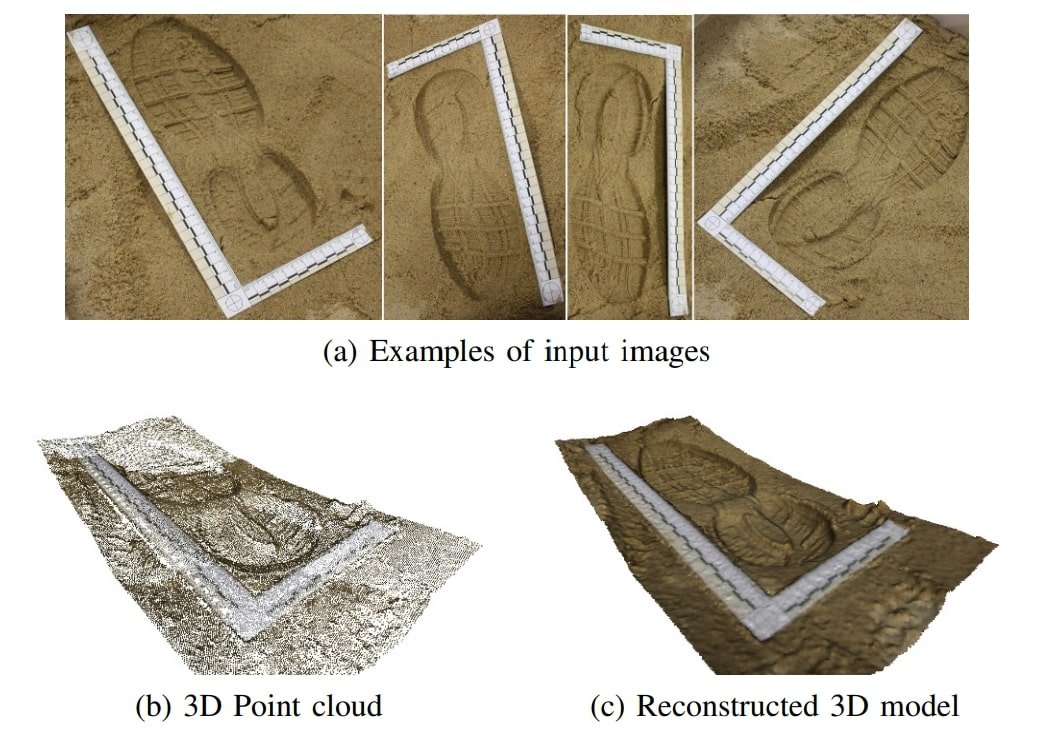
In 2012, researchers utilized multi-view, stereo methods to acquire a three-dimensional mannequin from images taken from a footwear impression, generally present in crime scenes. Of their strategy, the purpose was to reconstruct shredded pictures. Their pipeline included photogrammetry and 3D reconstruction of the impressions, which collectively produced a whole 3D mannequin from a group of images taken at totally different angles across the impression.
6. Face Recognition in Authorized Investigations
Maybe essentially the most relevant pc imaginative and prescient know-how in regulation circumstances is facial recognition. In regulation enforcement, facial recognition is utilized for surveillance, alarm, and crime prevention, and several other firms are growing software program to make it simpler.
Recognizing totally different facial feelings will help detect when an individual might have been concerned in against the law both as a perpetrator or an eyewitness. The face recognition system ought to have the ability to detect sure expressions in folks’s faces which will point out guilt, or that an individual is protecting secret data that’s of curiosity for the crime dedicated. CV strategies and instruments have confirmed to be worthwhile in fixing crimes or detecting doable legal actions.

There are image-based and feature-based strategies for face detection. Characteristic-based strategies attempt to discover invariant options of faces for detection, whereas image-based strategies attempt to study templates from examples in pictures. Datasets for face recognition embrace:
- PASCAL FACE – comprises 1335 labeled faces in 851 pictures with massive face look and pose variations
- AWF (Annotated Faces in Wild dataset) – contains 205 pictures with 473 labeled faces.
- MIT – CBCL dataset, comprises a coaching set (2429 faces, 4548 non-faces) and a check set (472 faces, 23573 non-faces).
7. Digital Courtrooms
Digital environments will be utilized in a number of court docket conditions. They will facilitate trial preparation, current proof and assist arguments throughout trials, query distant witnesses, and supply a recording of the trials. This know-how can be utilized primarily by attorneys for displays to the choose (or jury), or to elicit reactions and opinions from consultants, both in preparation for or at trial. VR can expose the scenario to the jury from the place of the events and witnesses to the crime occasions.

Alternatively, videoconference can be utilized to supply testimony and cross-examination of distant witnesses and knowledgeable witnesses throughout authorized processes. The people who find themselves not in a position to attend the trial can nonetheless present worthwhile testimony by utilizing VC/VR know-how. At present, researchers are exploring the probabilities of utilizing digital environments as an alternative to videoconferencing.
8. Compliance Monitoring
The development business is likely one of the most harmful sectors regarding occupational security due to the dynamic and messy atmosphere at building websites. Security and compliance are complementary to one another and are essential for managing the protected circumstances at building. Laptop Imaginative and prescient methods in civil engineering is usually a key element for improved monitoring by way of security and compliance circumstances. To satisfy security and compliance necessities in building – some researchers have utilized superior CV and deep studying strategies.
M. Nain and his crew (2020) examined numerous CV frameworks together with deep studying, to realize environment friendly and cost-effective security (compliance monitoring). They utilized picture classification and detection by SVM (Help Vector Machines). Additionally, deep studying utilizing CNNs and RNNs (Recurrent Neural Networks) was used to extract options mechanically. They concluded that the most effective algorithms for real-time problem detection are YOLO, SSD, RetinaNet, and R-FCN.
9. Proof Authentication
An necessary activity within the regulation (authorized) techniques is the proof evaluation. Classical strategies of reviewing proof, reminiscent of pictures, movies, and authorized paperwork, are time-consuming and error-prone. AI techniques can rapidly and precisely analyze proof, marking related particulars and discovering errors that may go unnoticed by authorized professionals or human observers. As well as, CV will help within the authentication of proof by detecting unauthorized adjustments or manipulations, thus guaranteeing the integrity of the judicial course of.
Making use of Laptop Imaginative and prescient for Authorized Functions
Authorized tech should combine pc imaginative and prescient and synthetic intelligence in regulation functions. By offloading menial, time-heavy, cost-burdensome duties by permitting computer systems to “see,” the authorized business will achieve the power to rapidly adapt and succeed with the ever-evolving authorized panorama.
Viso Suite provides enterprises the power to simply resolve complicated enterprise challenges with out a single line of code. To get began utilizing pc imaginative and prescient for options on this planet of regulation and regulation, e-book a demo with us.

