Attacking picture recognition programs with carefully-crafted adversarial photographs has been thought-about an amusing however trivial proof-of-concept during the last 5 years. Nevertheless, new analysis from Australia means that the informal use of extremely well-liked picture datasets for business AI tasks might create an everlasting new safety drawback.
For a few years now, a bunch of lecturers on the College of Adelaide has been making an attempt to clarify one thing actually vital about the way forward for AI-based picture recognition programs.
It’s one thing that may be tough (and really costly) to repair proper now, and which might be unconscionably pricey to treatment as soon as the present traits in picture recognition analysis have been absolutely developed into commercialized and industrialized deployments in 5-10 years’ time.
Earlier than we get into it, let’s take a look at a flower being categorized as President Barack Obama, from one of many six movies that the workforce has revealed on the project page:
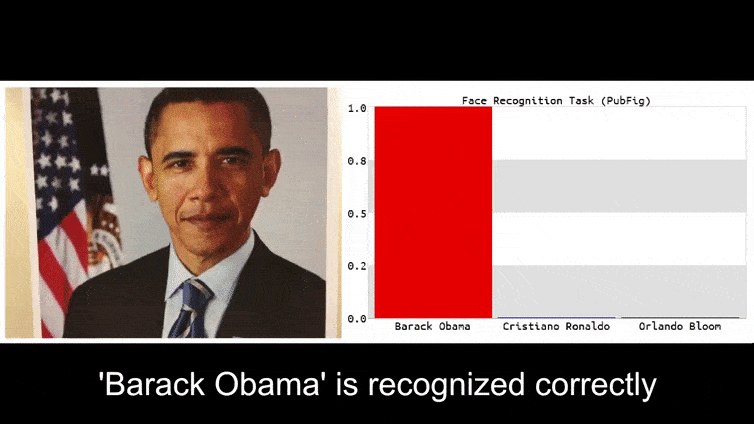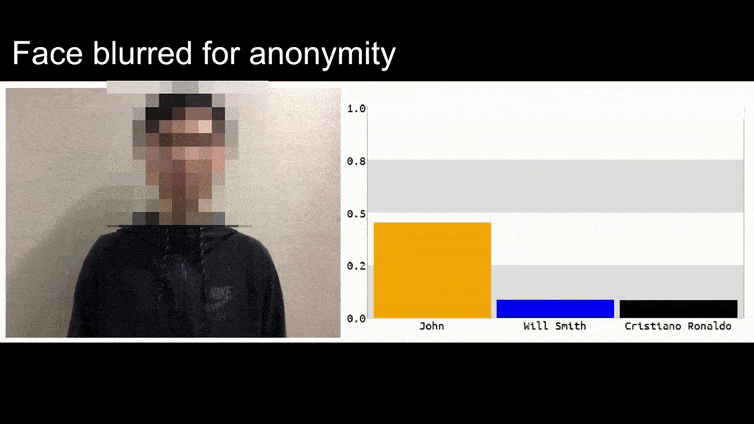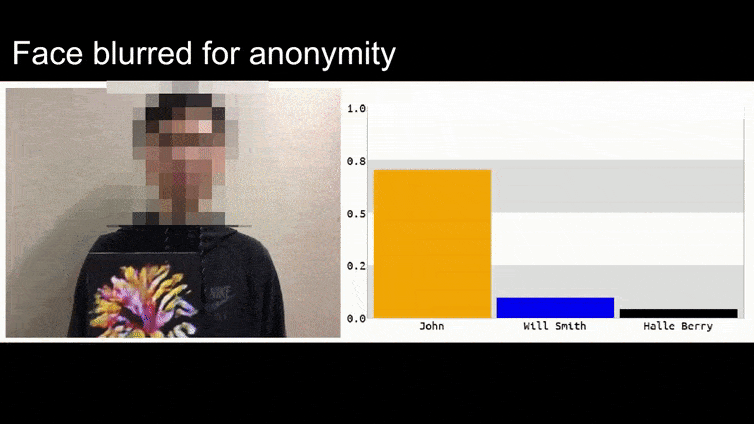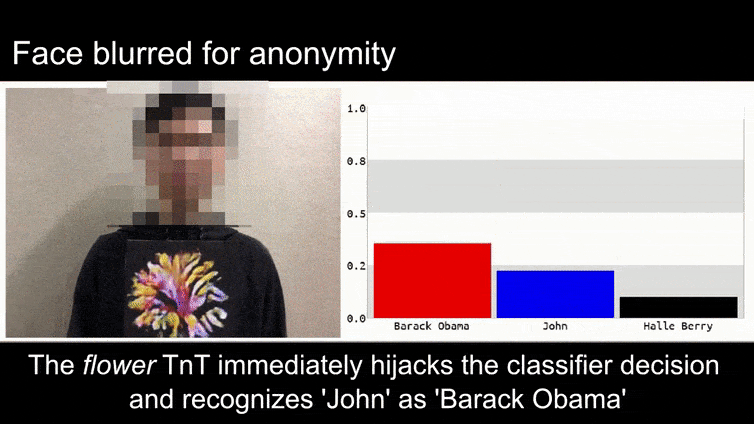
Supply: https://www.youtube.com/watch?v=Klepca1Ny3c
Within the above picture, a facial recognition system that clearly is aware of how one can acknowledge Barack Obama is fooled into 80% certainty that an anonymized man holding a crafted, printed adversarial picture of a flower can also be Barack Obama. The system doesn’t even care that the ‘pretend face’ is on the topic’s chest, as an alternative of on his shoulders.
Though it’s spectacular that the researchers have been capable of accomplish this type of id seize by producing a coherent picture (a flower) as an alternative of simply the same old random noise, plainly goofy exploits like this crop up pretty recurrently in safety analysis on laptop imaginative and prescient. As an example, these weirdly-patterned glasses that had been capable of idiot face recognition back in 2016, or specially-crafted adversarial photographs that try to rewrite highway indicators.
In the event you’re , the Convolutional Neural Community (CNN) mannequin being attacked within the above instance is VGGFace (VGG-16), skilled on Columbia College’s PubFig dataset. Different assault samples developed by the researchers used completely different sources in numerous combos.

A keyboard is re-classed as a conch, in a WideResNet50 mannequin on ImageNet. The researchers have additionally ensured that the mannequin has no bias in direction of conches. See the complete video for prolonged and extra demonstrations at https://www.youtube.com/watch?v=dhTTjjrxIcU
Picture Recognition as an Rising Assault Vector
The various spectacular assaults that the researchers define and illustrate should not criticisms of particular person datasets or particular machine studying architectures that use them. Neither can they be simply defended towards by switching datasets or fashions, retraining fashions, or any of the opposite ‘easy’ cures that trigger ML practitioners to scoff at sporadic demonstrations of this type of trickery.
Quite, the Adelaide workforce’s exploits exemplify a central weak spot in the complete present structure of picture recognition AI growth; a weak spot which might be set to show many future picture recognition programs to facile manipulation by attackers, and to place any subsequent defensive measures on the again foot.
Think about the most recent adversarial assault photographs (such because the flower above) being added as ‘zero-day exploits’ to safety programs of the longer term, simply as present anti-malware and antivirus frameworks replace their virus definitions daily.
The potential for novel adversarial picture assaults can be inexhaustible, as a result of the muse structure of the system didn’t anticipate downstream issues, as occurred with the internet, the Millennium Bug and the leaning Tower of Pisa.
In what method, then, are we setting the scene for this?
Getting the Information for an Assault
Adversarial photographs such because the ‘flower’ instance above are generated by getting access to the picture datasets that skilled the pc fashions. You don’t want ‘privileged’ entry to coaching information (or mannequin architectures), since the most well-liked datasets (and lots of skilled fashions) are broadly obtainable in a strong and constantly-updating torrent scene.
As an example, the venerable Goliath of Pc Imaginative and prescient datasets, ImageNet, is available to Torrent in all its many iterations, bypassing its customary restrictions, and making obtainable essential secondary parts, comparable to validation sets.

Supply: https://academictorrents.com
When you have the information, you may (because the Adelaide researchers observe) successfully ‘reverse-engineer’ any well-liked dataset, comparable to CityScapes, or CIFAR.
Within the case of PubFig, the dataset which enabled the ‘Obama Flower’ within the earlier instance, Columbia College has addressed a rising pattern in copyright points round picture dataset redistribution by instructing researchers how one can reproduce the dataset through curated hyperlinks, fairly than making the compilation straight obtainable, observing ‘This appears to be the best way different giant web-based databases appear to be evolving’.
Usually, that’s not crucial: Kaggle estimates that the ten hottest picture datasets in laptop imaginative and prescient are: CIFAR-10 and CIFAR-100 (each directly downloadable); CALTECH-101 and 256 (each obtainable, and each presently obtainable as torrents); MNIST (officially available, additionally on torrents); ImageNet (see above); Pascal VOC (available, additionally on torrents); MS COCO (available, and on torrents); Sports activities-1M (available); and YouTube-8M (available).
This availability can also be consultant of the broader vary of obtainable laptop imaginative and prescient picture datasets, since obscurity is loss of life in a ‘publish or perish’ open supply growth tradition.
In any case, the shortage of manageable new datasets, the excessive value of image-set growth, the reliance on ‘previous favorites’, and the tendency to simply adapt older datasets all exacerbate the issue outlined within the new Adelaide paper.
Typical Criticisms of Adversarial Picture Assault Strategies
Probably the most frequent and protracted criticism of machine studying engineers towards the effectiveness of the most recent adversarial picture assault method is that the assault is particular to a selected dataset, a selected mannequin, or each; that it isn’t ‘generalizable’ to different programs; and, consequently, represents solely a trivial menace.
The second-most frequent grievance is that the adversarial picture assault is ‘white field’, that means that you’d want direct entry to the coaching atmosphere or information. That is certainly an unlikely state of affairs, usually – as an illustration, in case you wished to take advantage of the coaching course of for the facial recognition programs of London’s Metropolitan Police, you’d should hack your method into NEC, both with a console or an axe.
The Lengthy-Time period ‘DNA’ of Standard Pc Imaginative and prescient Datasets
Concerning the primary criticism, we must always take into account not solely {that a} mere handful of laptop imaginative and prescient datasets dominate the business by sector year-on-year (i.e. ImageNet for a number of forms of object, CityScapes for driving scenes, and FFHQ for facial recognition); but in addition that, as easy annotated picture information, they’re ‘platform agnostic’ and extremely transferable.
Relying on its capabilities, any laptop imaginative and prescient coaching structure will discover some options of objects and lessons within the ImageNet dataset. Some architectures might discover extra options than others, or make extra helpful connections than others, however all ought to discover not less than the highest-level options:

ImageNet information, with the minimal viable variety of right identifications – ‘excessive stage’ options.
It’s these ‘high-level’ options that distinguish and ‘fingerprint’ a dataset, and that are the dependable ‘hooks’ on which to hold a long-term adversarial picture assault methodology that may straddle completely different programs, and develop in tandem with the ‘previous’ dataset because the latter is perpetuated in new analysis and merchandise.
A extra subtle structure will produce extra correct and granular identifications, options and lessons:

Nevertheless, the extra an adversarial assault generator depends on these decrease options (i.e. ‘Younger Caucasian Male’ as an alternative of ‘Face’), the much less efficient it will likely be in cross-over or later architectures that use completely different variations of the unique dataset – comparable to a sub-set or filtered set, the place most of the authentic photographs from the complete dataset should not current:

Adversarial Assaults on ‘Zeroed’, Pre-Educated Fashions
What about instances the place you simply obtain a pre-trained mannequin that was initially skilled on a extremely well-liked dataset, and provides it utterly new information?
The mannequin has already been skilled on (as an illustration) ImageNet, and all that’s left are the weights, which can have taken weeks or months to coach, and at the moment are prepared that can assist you establish comparable objects to people who existed within the authentic (now absent) information.

With the unique information faraway from the coaching structure, what’s left is the ‘predisposition’ of the mannequin to categorise objects in the best way that it initially discovered to do, which can primarily trigger most of the authentic ‘signatures’ to reform and turn out to be susceptible as soon as once more to the identical previous Adversarial Picture Assault strategies.
These weights are worthwhile. With out the information or the weights, you primarily have an empty structure with no information. You’re going to have to coach it from scratch, at nice expense of time and computing sources, similar to the unique authors did (in all probability on extra highly effective {hardware} and with a better funds than you may have obtainable).
The difficulty is that the weights are already fairly well-formed and resilient. Although they’ll adapt considerably in coaching, they’re going to behave equally in your new information as they did on the unique information, producing signature options that an adversarial assault system can key again in on.
In the long run, this too preserves the ‘DNA’ of laptop imaginative and prescient datasets which might be twelve or more years old, and will have handed by a notable evolution from open supply efforts by to commercialized deployments – even the place the unique coaching information was utterly jettisoned at the beginning of the venture. A few of these business deployments might not happen for years but.
No White Field Wanted
Concerning the second widespread criticism of adversarial picture assault programs, the authors of the brand new paper have discovered that their potential to deceive recognition programs with crafted photographs of flowers is very transferable throughout a variety of architectures.
While observing that their ‘Common NaTuralistic adversarial paTches’ (TnT) methodology is the primary to make use of recognizable photographs (fairly than random perturbation noise) to idiot picture recognition programs, the authors additionally state:
‘[TnTs] are efficient towards a number of state-of-the-art classifiers starting from broadly used WideResNet50 within the Massive-Scale Visible Recognition activity of ImageNet dataset to VGG-face fashions within the face recognition activity of PubFig dataset in each focused and untargeted assaults.
‘TnTs can possess: i) the naturalism achievable [with] triggers utilized in Trojan assault strategies; and ii)the generalization and transferability of adversarial examples to different networks.
‘This raises security and safety considerations concerning already deployed DNNs in addition to future DNN deployments the place attackers can use inconspicuous natural-looking object patches to misguide neural community programs with out tampering with the mannequin and risking discovery.’
The authors recommend that typical countermeasures, comparable to degrading the Clear Acc. of a community, might theoretically present some protection towards TnT patches, however that ‘TnTs nonetheless can efficiently bypass this SOTA provable protection strategies with many of the defending programs reaching 0% Robustness’.
Doable different options embrace federated studying, the place the provenance of contributing photographs is protected, and new approaches that might straight ‘encrypt’ information at coaching time, comparable to one lately prompt by the Nanjing College of Aeronautics and Astronautics.
Even in these instances, it will be vital to coach on genuinely new picture information – by now the photographs and related annotations within the small cadre of the most well-liked CV datasets are so embedded in growth cycles world wide as to resemble software program greater than information; software program that usually hasn’t been notably up to date in years.
Conclusion
Adversarial picture assaults are being made attainable not solely by open supply machine studying practices, but in addition by a company AI growth tradition that’s motivated to reuse well-established laptop imaginative and prescient datasets for a number of causes: they’ve already proved efficient; they’re far cheaper than ‘ranging from scratch’; they usually’re maintained and up to date by vanguard minds and organizations throughout academia and business, at ranges of funding and staffing that may be tough for a single firm to copy.
Moreover, in lots of instances the place the information shouldn’t be authentic (unlike CityScapes), the photographs had been gathered previous to current controversies round privateness and data-gathering practices, leaving these older datasets in a sort of semi-legal purgatory which will look comfortingly like a ‘secure harbor’, from an organization’s standpoint.
TnT Attacks! Universal Naturalistic Adversarial Patches Against Deep Neural Network Systems is co-authored by Bao Gia Doan, Minhui Xue, Ehsan Abbasnejad, Damith C. Ranasinghe from the College of Adelaide, along with Shiqing Ma from the Division of Pc Science at Rutgers College.
Up to date 1st December 2021, 7:06am GMT+2 – corrected typo.

